Heather Wright/The Independent
TransForm Shared Services and Bluewater Health now say it could be mid-December before its able to recover from a hack which has affected patient services.
While the hospitals deal with the fall out from the ransomware attack, the OPP, Interpol and the FBI are working with the southwestern Ontario health care organizations on the data breach and have kept a tight lid on any information about what is going on behind the scenes in the investigation.
But people who follow hacks in the health care community have uncovered who the hackers are and in one case, have seen the pilfered data and talked with the criminal group.
Databreaches.net outed the hackers as Daixin. The blogger behind the website has not only seen some of the 5.6 million pieces of data Daixin stole from Bluewater Health, they talked with Daixin on the dark web.
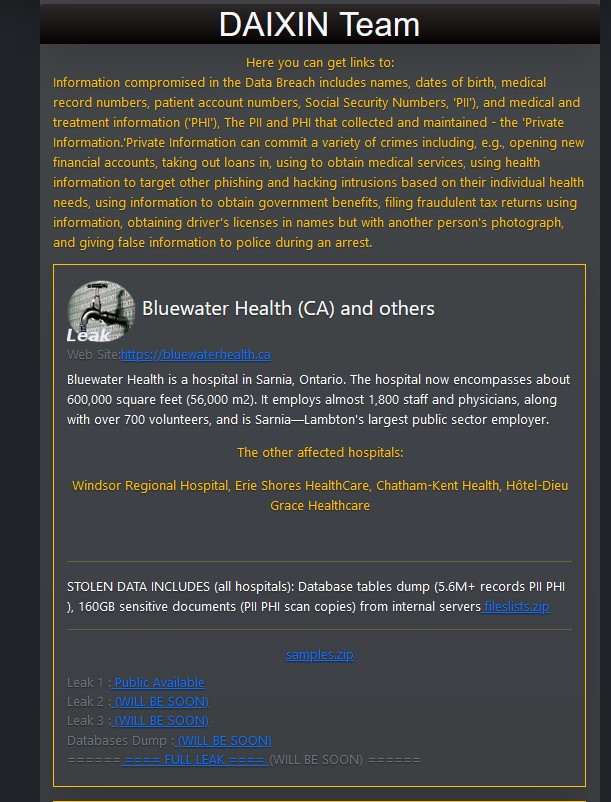
In a Nov. 1 post, DataBreaches.net reported the Oct. 23 attack, saying the hackers destroyed any backup records as well.
“They knew from the beginning that we had quite a bit of critical data from their internal resources and we weren’t bluffing,” Daixin told DataBreaches.
“After much deliberation, they wrote that they were not going to pay.”
DataBreaches earned the trust of the hackers after investigating a number breaches linked to Daixin a. This time, Daixin said they gained access to Bluewater Health’s system through TransForm Services – the hospital’s IT provider – a week before they deployed the ransomware, Databreaches.net told The Independent.
It took the hacker a few hours to take over the system, the website reports. “The networks were completely transparent – we could go anywhere,” Daixin told DataBreaches, adding it was easier to access the system because passwords had been used over and over again.
“We could have been in their system for a very long time and destroyed almost everything – down to the last device (including medical),” Daixin claimed. “We didn’t do that, we just left.”
Brett Callow a threat analyst is with Emsisoft. His company deals with cyber security threats to patient data. He also found the Bluewater Health data on the dark web however he did not access it.
Callow says Daixin is a relatively new player in ransomware – an illegal activity that takes computer data hostage for cash. Ransomware has been around for a couple of decades but has reached “its current epidemic levels” in 2019 and “has been bad ever since.”
Callow says Daixin “has been operating under that brand name since the middle of last year. They had attacks on the multiple health care organizations, as well as multiple organizations in other sectors. Their demands range from a million bucks north.”
Most ransomware is created in Russia and Eastern Europe, says Callow, but it’s not easy to pin down where the hackers are using it.
“The people who use it to carry out the attacks can be based absolutely anywhere.” And, Callow says, most are financially motivated.
Ransomware demands can be very steep. “The highest demand known is $214 million – that one wasn’t paid. The highest was paid is $40 million,” Callow says noting neither were in the health care field.
Daixin claimed in its interview with DataBreaches the hospital refused to negotiate instead pleading to release the data.
With over 12 hours before Daixin’s deadline expired, according to DataBreaches, negotiators using the name ‘Bluewater Health and others’ wrote; “We have strongly considered your demands, but we cannot pay. We have to use our money, all of our money, for our patients.
“We understand that this will upset you. But please know this: cancer treatment is being cancelled. Surgeries are being postponed. Our patients are hurting. We are doing our best to restore our operations, and we will recover. But this attack has resulted in actual pain and suffering.
“We cannot pay, and we are asking you to delete the data and leave us alone. Our patients and staff have endured enough.”
When the deadline expired, Daixin started dumping data, telling DataBreaches they probably “would have settled for $4 million.”
Callow says even if the hospital had paid, there would be no guarantee the hackers would have deleted the data it had. And, he says, the key to open up the network would not have solved all the problems instantly.
There has now been three dumps of Bluewater Health information. DataBreaches has viewed all three, including patient information including information about COVID vaccines and medication.
There is also sensitive internal documents like complaints about patient care which named the hospital employee who is the subject of the complain and information about “Morbidity & Mortality” forums which are normally “secure and confidential so that staff can share information about a case frankly and freely and learn from it.”
Daixin has not released all the information yet, however DataBreaches expects it will shortly and may be sold to data brokers.
Bluewater Health is not alone in its computer hacking dilemma. Callow says it is unfortunate but more hospitals are victims of hackers than ever before.
“The government’s response to the ransomware problem as the woefully inadequate both in Canada and in other countries. They now try to do a bit more than they’ve done in the past,” noted Callow saying Nov. 2, a number of nations, including Canada, signed a manifesto saying they would not pay ransom.
“It is really a case of too little, too late. Ransomware gangs now have massive resources, multiple, multiple millions of dollars. This is a huge industry where people stand to make absolutely massive amounts of money and is now a lot more challenging to deal with than it would have been some nipped in the bud in the early days.”





